Regulatory compliant data security to protect PHI, PII, and vulnerability assessment with ransomware protection for endpoint security
Application Security testing of software or app on the Cloud will help to eliminate vulnerabilities from applications before they are placed into production and deployed. Our team will identify all the issues and provide a detailed report of fixes that need to make the product secured.
Web application attacks represent the greatest threat to an organization’s security.
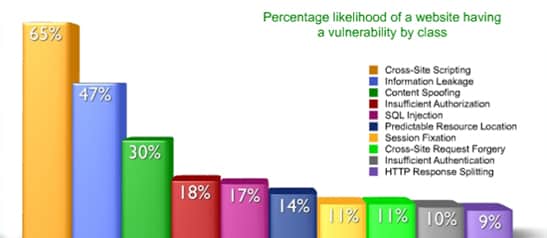
Website Vulnerability to Attack
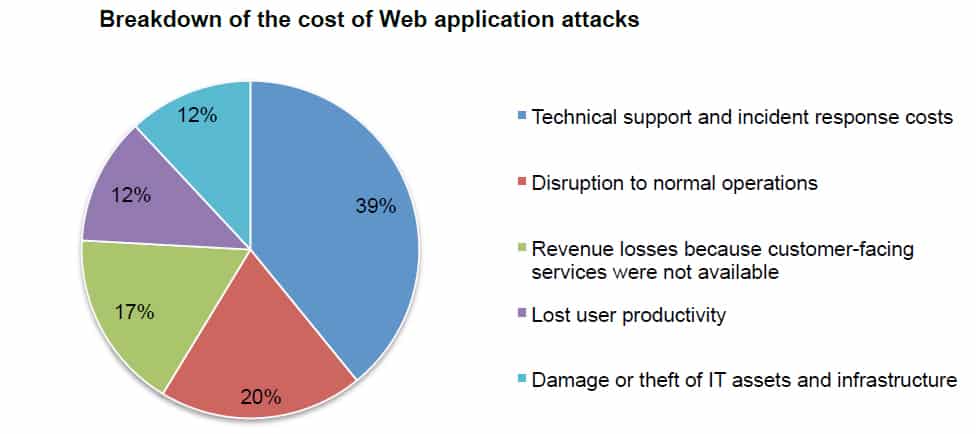
Web Application Attacks
What is Application Security Testing?
A form of stress testing, which exposes weaknesses or flaws in a Web Application, Art of finding ways to exploit Web Application.
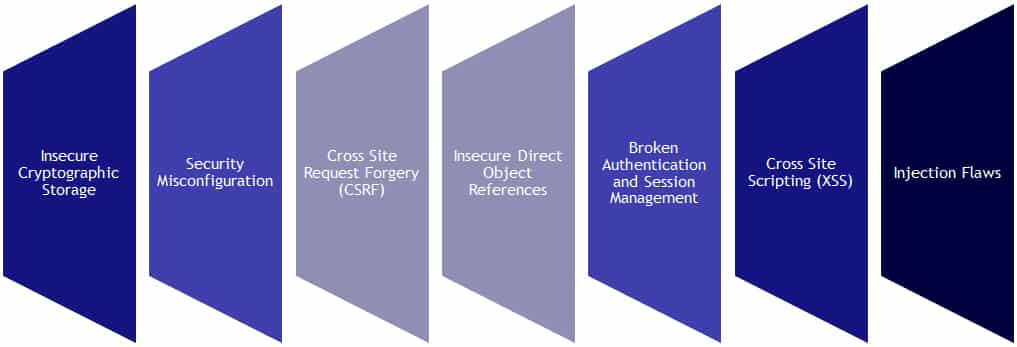
Application Security Testing
Our Approach:
Authentication Assessment (Grey Box Assessment)
- Dynamic Pages / Static Pages
- Login Page
- Provided with Login Credentials
Non-AuthenticationAssessment (Black Box Assessment)
- Dynamic Pages / Static Pages
- Publicly Available Pages
- Login Page / No login page
- Not Provided with Login Credentials
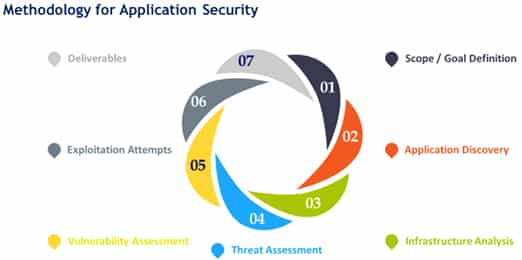
Methodology for Application Security
- Scope/Goal Definition
-
- What type of Assessment is to be conducted
- Authenticated Assessment
- Non-Authenticated Assessment
- Which Web Application the test will be conducted
- Duration of the test
- What type of Assessment is to be conducted
- Application Discovery
-
- Web application discovery is a process aimed at identifying web applications on a given infrastructure. The latter is usually specified as a set of IP addresses (maybe a netblock) but may consist of a set of DNS symbolic names or a mix of the two.
- This information is handed out before the execution of an assessment of an application-focused assessment.
- Infrastructure Analysis
-
- Analyzing to find the location of Web Application in the Infrastructure.
- Check for the details of how is Web Server, Application Server, and Database Server Located.
- Do the analysis of what is placed to protect the Web Server & find out gaps in the placement.
- Threat Assessment
-
- Threat Assessment is conducted based on the findings of Step 2 and Step 3.
- All the possible Threat related to the Application and Infrastructure are Assessed in this phase.
- Vulnerability Assessment
Tool Based Scan is conducted based on the scope defined in step 1
- Authentication Assessment (Grey Box Assessment)
- Dynamic Pages / Static Pages
- Login Page
- Provided with Login Credentials
- Non-Authentication Assessment (Black Box Assessment)
- Dynamic Pages / Static Pages
- Publically Available Pages
- Login Page / No login page
- Not Provided with Login Credentials
Our Consultant team does analysis based on manual intelligence.
- False Positive / False Negative
- Our team conducts analysis to find False Positive and False Negative.
- Vulnerabilities are rated as Critical, High, Medium, and Low after the analysis.
- Exploitation Attempts
HAS Two Sub Stages
- Attack & Penetration
- Known / available exploit selection – Tester acquires publicly available s/w for exploiting.
- Exploit customization – Customize exploits s/w program to work as desired.
- Exploit development – Develop own exploit if no exploit program is available
- Exploit testing – Exploit must be tested before a formal Test to avoid damage.
- Attack – Use of exploit to gain unauthorized access to a target.
- Privilege Escalation
- What can be done with acquired access/privileges
- Alter
- Damage
- What not
Our team of consultants will be conducting POC to exploit Critical and High Vulnerabilities.
- Deliverables
Organize Data/related results for Management Reporting
-
- Consolidation of Information Gathered
- Analysis and Extraction of General Conclusions
- Recommendations
Contact Bob Mehta at Bob@hipaatraining.net on the next steps to get a quote for the services.
USER RATING:
Application Security Assessment Services is rated 4.8 out of 5 by 187 users.
